We live in an era where our physical movements leave a digital residue as permanent as ink on paper. Over the years, geofencing has evolved from a helpful navigational tool into a pervasive surveillance infrastructure with very real privacy issues. The convenience of a smartphone nudging you with a coupon when you walk past a coffee shop seems harmless on the surface. However, beneath that simple interaction lies a complex web of geofencing protocols, data exchanges, and potential violations of civil liberties.
For the small business owner, geofencing is a marketing miracle. For the privacy advocate, it is a Pandora’s Box. The central question we must answer is no longer can we track a user, but should we? And if we do, how do we ensure we aren’t crossing the invisible line between personalized service and “Big Brother” intrusion? This article will dissect the anatomy of geofencing privacy issues, exploring the mechanics of data capture, the terrifying reality of “reverse location” warrants, and the new wave of legislation like California’s AB-45 and the Fifth Circuit’s landmark 2024 ruling that is reshaping the landscape.
If you use geofencing in your business, be sure to look at the template at the end of the article as an addition to your privacy policy.
The Mechanics of Intrusion: How Data is Exposed
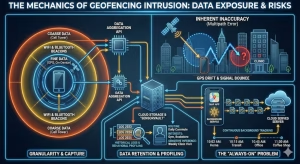
To understand the privacy risks, we must first look under the hood of the technology. Geofencing is not simply drawing a circle on a map; it is a trigger mechanism based on Latent Semantic Indexing (LSI) of physical location data. When a mobile device enters a defined virtual perimeter, or “fence,” it triggers a pre-programmed action. This action relies on the device constantly broadcasting its location.
Granularity of Location Data
The precision of this data varies wildly, and that variance is where privacy issues often arise. We deal with two main types of data:
-
Coarse Data: This comes from cell tower triangulation. It is broad, often covering several city blocks. It is generally less intrusive but also less useful for targeted geofencing.
-
Fine Data: This is derived from GPS, Wi-Fi access points, and Bluetooth beacons. This can pinpoint a user to within a few meters.
The privacy issue here is the “Always-On” problem. Many apps request location permissions to function in the background. Even when you aren’t using the app, its API (Application Programming Interface) may be pinging your location to a server every few minutes. This creates a detailed log of your daily routine, where you sleep, where you work, and who you visit. This “fine” data is what fuels the most effective geofencing campaigns, but it is also what creates the most significant liability.
Inherent Inaccuracy & False Positives
We must highlight that GPS is not magic. It suffers from technical limitations like “multipath errors,” where satellite signals bounce off tall buildings before hitting your phone. This causes the reported location to drift, sometimes by 50 meters or more.
-
The Risk: In a geofencing context, this “drift” can place a user inside a sensitive area, like a crime scene or a rehab clinic, when they were actually just walking by on the sidewalk.
-
The Consequence: False positives in marketing are annoying; false positives in law enforcement or insurance profiling can ruin lives. Imagine being denied life insurance because a geofencing error placed you repeatedly at a high-risk facility you never entered.
Data Retention
The most dangerous data is the data you keep. Many companies store location logs indefinitely. This historical data, often called “breadcrumbs,” allows for retrospective profiling. A single data point tells you where someone is; a year of data points tells you who they are.
Core Privacy Concerns for Consumers
The average consumer rarely reads the Terms of Service. They click “Allow” because they want the app to work. This consent is often uninformed, leading to a sense of betrayal when the extent of the tracking is revealed.
Surveillance Creep
We have witnessed a shift from “service-based” tracking to “surveillance-based” tracking. Service-based tracking is when you use Uber; the app needs to find you to pick you up. Once the ride is over, the tracking should stop. Surveillance-based tracking is when a retail app tracks your movements through a competitor’s store to serve you a conquest ad. This use of geofencing transforms the consumer from a client into a target.
Sensitive Location Inference
Algorithms are now capable of inferring highly sensitive attributes based solely on location history.
-
Health Status: Frequent visits to an oncologist or a dialysis center.
-
Religious Beliefs: Weekly attendance at a specific church, mosque, or synagogue.
-
Political Affiliation: Presence at a political rally or protest.
In 2025, this is not theoretical. With the passage of AB-45 in California, dealing specifically with reproductive health data, the legal system is acknowledging that where you go defines your most private medical realities. Using geofencing around these sensitive zones is now a legal minefield.
Stalking and Safety
Real-time location sharing features, like the “Snap Map” or “Find My,” are popular among younger demographics. However, if this data is intercepted or if the geofencing perimeters are set by malicious actors, it poses a severe physical safety risk. Stalkers can use geofencing tools to get alerts when a victim leaves work or arrives home.
The Legal Dragnet: Geofence Warrants
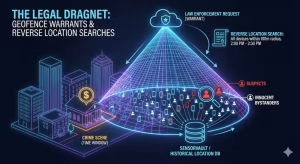
Perhaps the most dystopian application of this technology is the “Geofence Warrant.” This is a technique used by law enforcement that flips the traditional concept of a search warrant on its head.
What is a Reverse Location Search?
Traditionally, police have a suspect and get a warrant to search their house or phone. A Geofence Warrant works in reverse. Police have a crime scene, a “place,” and they ask a tech giant (usually Google or Apple) to identify everyone who was within a specific geofencing radius during a specific time window.
-
The Command: “Tell us every device ID that was within 100 meters of this bank between 2:00 PM and 2:30 PM.”
-
The Result: A list of innocent bystanders, witnesses, and potentially the perpetrator.
Constitutional Issues
This practice raises massive Fourth Amendment concerns regarding unreasonable search and seizure. The Fourth Amendment was designed to prevent “general warrants,” dragnets where officers search everyone in a town to find one criminal.
-
Case Study: United States v. Smith (2024): In a landmark decision, the Fifth Circuit Court of Appeals ruled that these warrants are categorically unconstitutional. They argued that because the search requires scanning the location history of millions of users to find the few in the geofencing zone, it violates the privacy of the masses. This split from the Fourth Circuit’s earlier rulings sets the stage for a Supreme Court showdown.
-
The “Sensorvault”: This term refers to Google’s massive internal database of historical location records. While useful for traffic data and ad targeting, it effectively serves as a comprehensive history of human movement, subject to subpoena at any moment.
Regulatory Landscape & Compliance (The “Rules of the Road”)

The “Wild West” days of location data are ending. In 2025, a patchwork of state and international laws governs how geofencing can be used.
GDPR (Europe)
The General Data Protection Regulation (GDPR) set the global standard. Under GDPR, location data is personal data.
-
Consent: You cannot hide geofencing consent in a 50-page user agreement. It must be a clear, affirmative “Opt-in.”
-
Right to be Forgotten: Users have the right to demand their location history be deleted.
CCPA & CPRA (California)
The California Consumer Privacy Act and its subsequent expansion (CPRA) define “Precise Geolocation” as a “Sensitive Personal Information” category.
-
The Right to Limit: Consumers can direct a business to limit the use of their sensitive data to only what is necessary for the immediate service. Marketing via geofencing often falls outside this “necessary” scope, meaning users can opt-out easily.
Maryland Online Data Privacy Act (MODPA)
Effective late 2025, Maryland has introduced one of the strictest laws in the nation. It includes a specific ban on geofencing around mental health and reproductive health facilities. It also mandates “data minimization,” meaning companies legally cannot collect location data unless it is strictly necessary for the product’s function, advertising does not count as “strictly necessary” under this framework.
COPPA (Children)
The Children’s Online Privacy Protection Act strictly bans collecting geolocation data from children under 13 without verifiable parental consent. Given that many apps with geofencing capabilities (games, social media) appeal to kids, this is a major area of liability.
Ethical Best Practices for Business
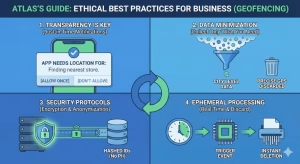
One thing for geofencing clients to know: “Just because you can track it, doesn’t mean you should.” Compliance is the floor; ethics is the ceiling. To build trust, aim for the ceiling.
Transparency is Key
Move away from legalese. Use “Just-in-Time” notifications.
-
Bad: “This app uses location services.”
- Good: “We need your location right now to show you the nearest store. We will not track you after you close this map.”Transparency builds trust. If a user understands why the geofencing trigger is helpful to them, they are more likely to opt-in.
Data Minimization
This is the golden rule of modern data science. Collect only what you need.
-
If you need to know what city a user is in for shipping estimates, do not request fine-grain GPS coordinates.
-
Ephemeral Processing: Process the geofencing trigger in real-time and then discard the location data immediately. Do not store a log of where that customer has been. If you don’t have the data, it can’t be stolen, and it can’t be subpoenaed.
Security Protocols
If you must store location data, treat it like toxic waste. It needs to be contained.
-
Encryption: Data must be encrypted in transit (from the phone to your server) and at rest (on your hard drive).
-
Anonymization: Never store location data attached to a name or email address. Use a hashed ID. While we know “anonymized” data can often be re-identified, it is a necessary first layer of defense.
Questions Answered about Geofencing Privacy Issues
How does geofencing violate privacy?
Geofencing violates privacy when it occurs without the user’s explicit, informed consent, or when the data collected is used for purposes other than what was agreed upon (e.g., selling your location history to insurance companies). The primary violation is the creation of a detailed profile of a person’s private life based on their movements.
Can I block geofencing?
Yes. The most effective method is to disable location services for specific apps in your smartphone’s settings. You can also use a VPN (Virtual Private Network) to mask your IP address, though this does not stop GPS-based geofencing. For total protection, a “Faraday bag” physically blocks all signals to the phone, rendering it invisible to the network.
Is geofencing legal for tracking employees?
It is generally legal to track employees using geofencing if they are using company-owned devices or vehicles during work hours. However, tracking an employee on their personal device, or tracking them off-hours, is a significant legal risk and often a violation of privacy. A clear, written policy is required.
What is a geofence warrant?
A geofence warrant is a court order issued to a tech company (like Google) requesting information on all devices that were present in a specific geographic area during a specific time frame. It is controversial because it targets groups of people rather than a specific suspect.
Future Trends: The War on Coordinates
The battle for location privacy is escalating. Here is what I see on the horizon.
On-Device Processing
Big Tech is realizing that holding user data is a liability. We are moving toward “on-device processing.” This means the geofencing logic happens on your phone’s chip. The phone knows it is near a Starbucks and pops up a notification, but it never tells the Starbucks server where you are. The data never leaves your pocket.
Blockchain & Geo-Privacy
New decentralized protocols are being developed where users can prove they are in a location (proof of location) without revealing their identity or exact coordinates to a central authority. This uses blockchain cryptography to verify location claims without exposing raw data.
Opt-Out by Default
Operating systems like iOS and Android are becoming more aggressive. We will likely see a future where “Opt-In” is the default for all tracking, and “Always Allow” location permissions are removed entirely or buried deep in developer settings. The era of passive tracking is ending.
Conclusion
The intersection of geography and technology is where I live my professional life. Geofencing is a tool of immense power. It can guide an ambulance to a crash site, or it can guide a predator to a victim. It can help a small coffee shop survive against a giant chain, or it can help a government suppress dissent.
The privacy issues surrounding geofencing are not technical glitches; they are fundamental questions about liberty in the digital age. We must balance Innovation with Integrity. For the business owner, this means collecting less and protecting more. For the consumer, it means staying vigilant and understanding the value of your own data.
We are building the digital infrastructure of the future. Let us ensure we do not build a prison.
A Template of an Addendum You Can Add to Your Privacy Policy for Geofencing
Most small businesses already have a standard privacy policy; this document acts as a specialized addendum or section specifically covering the high-risk area of location data. It incorporates the “Data Minimization” and “Transparency” principles we discussed, ensuring compliance with the stricter 2025 regulatory landscape (CCPA, GDPR, MODPA).
IMPORTANT DISCLAIMER
From WebHeads United: Though we write about geofencing and technology topics, we are not an attorney. While this template is based on current best practices and 2025 compliance standards (like CCPA and GDPR), it does not constitute legal advice. You must have your legal counsel review and approve this language before publishing it to ensure it meets the specific laws of your jurisdiction.
Location Services & Geofencing Privacy Addendum
Instructions:
-
Replace any text in [BOLD BRACKETS] with your specific company details.
-
Remove the “Note to Client” sections before publishing.
1. Location Data and Geofencing
At [YOUR COMPANY NAME], we use location-based technology to improve your experience and provide relevant services. This section explains what location data we collect, why we collect it, and how you can control it.
A. What We Collect
We may collect information about your location when you use our [WEBSITE / MOBILE APP]. This includes:
-
Coarse Location: An approximate location derived from your IP address (usually at the city or zip code level).
-
Precise Geolocation: With your explicit permission, we collect exact location data using GPS, Wi-Fi, Bluetooth signals, or cell tower triangulation.
Note to Client: Only include “Precise Geolocation” if you actually request GPS permissions in your app.
B. How We Use Geofencing
We utilize “Geofencing” technology. A geofence is a virtual perimeter around a real-world location (such as our store or a specific event).
-
The Trigger: When your device enters or exits one of our geofenced areas, it may trigger a notification, an offer, or a check-in alert on your device.
-
The Purpose: We use this strictly to [DESCRIBE PURPOSE, e.g., send you coupons when you are nearby / notify you when your order is ready for pickup].
-
Data Minimization: We do not track your movements continuously. We only register a “location event” when you interact with our specific geofenced zones.
C. Sensitive Locations (Our Promise)
In compliance with ethical standards and 2025 regulations:
-
We DO NOT place geofences around sensitive locations such as healthcare facilities, places of worship, mental health centers, or domestic abuse shelters.
-
We DO NOT use location data to infer health status, religious beliefs, or political affiliations.
2. Your Control and Choices
Your location data belongs to you. We provide the following controls:
-
Opt-In Consent: We will never collect precise GPS data without your permission. You will be asked to “Allow” location services when you first use the feature.
-
Opt-Out/Disable: You can revoke this permission at any time by going to your device settings:
-
iOS: Settings > Privacy > Location Services > [APP NAME] > Select “Never” or “Ask Next Time.”
-
Android: Settings > Location > App Permission > [APP NAME] > Select “Don’t Allow.”
-
-
Data Deletion: You have the right to request that we delete your historical location data. Please contact us at [INSERT PRIVACY EMAIL] to submit this request.
3. Data Retention and Security
-
Ephemeral Processing: Wherever possible, we process your location usage in real-time on your device. Once the “geofence trigger” (e.g., the coupon notification) is sent, the specific coordinate data is [DISCARDED / ANONYMIZED].
-
Storage: If we must store location data (e.g., for analytics), it is stored separately from your personal profile (name/email) and is encrypted using industry-standard protocols.
-
No Sale of Data: We [DO NOT / DO] sell your precise location history to third-party data brokers or insurance companies.
Note to Client: If you sell data, you must legally disclose it here and provide a “Do Not Sell My Info” link. As an expert, I strongly advise you NOT to sell location data to third parties.
4. Third-Party Services
We may use third-party providers (such as Google Maps API or a marketing platform) to facilitate our geofencing services. These partners are contractually obligated to protect your data and are prohibited from using your specific location history for their own independent purposes outside of providing the service to us.