Consider the modern consumer journey: a potential customer passes a storefront, and at that precise moment, their mobile device presents a contextually relevant offer for that very business. This seamless interaction is not an accident of marketing but the result of a precise, automated system. While many are familiar with the outcomes of such location-aware technology, the underlying architecture that initiates these actions often remains obscure. The gap between observing the effect and comprehending the cause prevents many businesses from leveraging one of the most powerful tools in their digital arsenal.
A functional understanding of basic geofence triggers is therefore not merely advantageous; it is a foundational requirement for executing effective proximity marketing. This analysis will deconstruct these mechanisms, providing a clear, technical examination of the core triggers and the location technologies that empower them.
What is a Geofence? A Prerequisite to Understanding Triggers
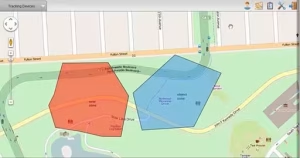
Before one can analyze the trigger mechanism, the boundary itself must be defined. A geofence is a virtual perimeter mapped onto a real-world geographic area. This perimeter can be as small as a single storefront or as large as a city district. It is created using geographic coordinates—typically latitude and longitude—to define its shape, which is most commonly a radius around a point or a polygon with multiple vertices. Think of it as a digital tripwire; it is dormant and invisible until a device interacts with its boundary.
It is critical to distinguish this concept from a related but distinct term: geotargeting. This is a common point of confusion that must be clarified.
- Geofencing is fundamentally a proactive, trigger-based system. Its core function is to initiate an action based on the real-time movement of a device relative to the virtual boundary. The logic is dynamic: when a user enters, an action occurs.
- Geotargeting, conversely, is a method of audience segmentation. It involves delivering content or advertisements to a group of users who are known to be in a specific geographic area, but it does not depend on the real-time crossing of a boundary. The logic is static: serve this ad to all users located within a certain zip code.
While both utilize location data, geofencing is about real-time events, whereas geotargeting is about defining an audience.
The Anatomy of a Geofence Trigger: The “If-Then” Logic
The “trigger” is the logical core of the entire geofencing apparatus. It is the programmatic event that connects the location-based condition to a predetermined action. At its most fundamental level, a geofence trigger operates on a simple conditional statement, often referred to as “If-This-Then-That” (IFTTT) logic.
The structure is as follows:
- IF (The Condition is Met): A device, through an installed application, reports a location change that satisfies the geofence’s criteria (e.g., crossing the boundary).
- THEN (The Action is Executed): The application or its backend server initiates a pre-configured action.
This action is not limited to push notifications. A robust geofencing strategy can trigger a wide array of automated responses, including sending SMS messages, dispatching emails, collecting vital location analytics for foot traffic analysis, displaying in-app content, or even enforcing security protocols in a Mobile Device Management (MDM) context, such as locking a corporate app when an employee leaves the office premises.
The 3 Types of Basic Geofence Triggers Explained
The “condition” component of the IFTTT logic is defined by one of three primary trigger types. Understanding the specific function of each is essential for designing an effective location-based campaign.
1. The Entry Trigger (Ingress)
An entry trigger, technically an OnEnterZone event, is activated at the precise moment a user’s device crosses from outside to inside the virtual perimeter. It is the most common trigger type, designed for immediate engagement.
- Use Case Example: A fast-casual restaurant establishes a geofence around its location. When a loyal customer with the restaurant’s app enters the geofence during lunch hours, an entry trigger sends a push notification: “Welcome back! Today’s special is the Chipotle Chicken Panini.”
- Business Value: This trigger facilitates a timely and contextual welcome, creates an immediate opportunity for upselling, and enhances the customer experience by demonstrating personalized awareness.
2. The Exit Trigger (Egress)
An exit trigger, or an OnExitZone event, is the inverse of the entry trigger. It activates when a device crosses the boundary from inside to outside. This trigger is exceptionally valuable for follow-up and data collection.
- Use Case Example: A car dealership places a geofence around its lot. If a customer who took a test drive leaves the premises without making a purchase, an exit trigger could initiate a delayed action—perhaps an email sent 30 minutes later from the sales associate asking for feedback on the vehicle.
- Business Value: It provides a mechanism for gathering customer feedback, re-engaging potential customers who have shown interest, and understanding points of friction in the customer journey.
3. The Dwell Trigger (Timed)
The dwell trigger is a more sophisticated condition that combines location with time. It activates only when a device remains inside a geofence for a specified duration. The logic is a two-part condition: IF (location_status == InsideZone) AND (time_elapsed >= T_dwell) THEN trigger_action, where $T_{dwell}$ represents the configured minimum time threshold.
- Use Case Example: A large home improvement store sets a geofence around its complex paint department. If a customer’s device remains in that zone for more than seven minutes (the
$T_{dwell}$), a dwell trigger sends a helpful push notification: “Have questions about paint finish or primer? Tap here to chat with an expert.” - Business Value: This trigger allows businesses to identify highly engaged—or potentially confused—customers and offer proactive assistance. It provides deeper behavioral insights than simple entry/exit data and creates opportunities for high-value, contextual interactions.
How Location is Determined: The Technology Behind the Trigger

The reliability of any geofence trigger is wholly dependent on the accuracy and timeliness of the underlying location data. Mobile devices utilize a fusion of technologies to determine their position, each with distinct characteristics regarding precision and power consumption.
Global Positioning System (GPS)
GPS operates by receiving signals from orbiting satellites. It offers the highest degree of accuracy in open, outdoor environments, often pinpointing a device within 5-10 meters. However, it is notoriously power-intensive and its signal is easily obstructed by buildings, making it less reliable for indoor use cases.
Wi-Fi
Wi-Fi positioning triangulates a device’s location based on its proximity to known Wi-Fi access points. In dense urban or indoor environments where GPS fails, Wi-Fi can provide reliable accuracy. Its precision is contingent on the density of Wi-Fi networks in the area and is generally less demanding on battery life than continuous GPS polling.
Cellular ID
The most battery-efficient method, cellular positioning, uses the device’s distance from multiple cell towers to approximate its location. While universally available, it is also the least precise method, with accuracy often varying from 100 to over 1,000 meters. This makes it suitable only for very large geofences, such as those encompassing a neighborhood or airport.
Bluetooth Low Energy (BLE) Beacons
For hyper-local or “micro” geofencing, BLE beacons are the superior technology. These are small, low-cost hardware transmitters. A device detects their signal only when in very close proximity (from a few inches to several meters). This allows for triggers at an extremely granular level, such as when a customer stands in front of a specific product display. The primary drawback is the requirement of physical hardware installation and maintenance.
Addressing Key Technical Questions & Concerns
Deploying geofencing technology necessitates an understanding of its practical limitations and requirements. The following points address the most frequent queries from businesses.
How Accurate is Geofencing?
The accuracy is not absolute; it is a function of the technology employed. For an outdoor event in a park, GPS-based accuracy is sufficient. For a specific aisle in a grocery store, BLE beacons are required. A successful strategy matches the location technology and the size of the geofence to the specific business objective to manage accuracy expectations.
Does Geofencing Drain a User’s Phone Battery?
This is a valid historical concern that has been largely mitigated by modern mobile operating systems. Both Android and iOS have developed highly efficient, low-power location monitoring services that intelligently switch between GPS, Wi-Fi, and cellular data to optimize for battery life. A well-engineered application will not cause significant battery drain, as it avoids continuous, high-accuracy GPS polling in favor of these optimized native services.
The Critical Role of User Permission
It must be unequivocally stated that geofencing is a permission-based technology. For any of this to function, a user must have explicitly granted the application permission to access their location data. Furthermore, businesses must be transparent in their privacy policies about how this data is used, in accordance with regulations like GDPR and CCPA. Trust is paramount; without user opt-in, the entire system is inert.
Conclusion: Leveraging Triggers for Strategic Advantage
The three basic geofence triggers—entry, exit, and dwell—are the foundational building blocks of sophisticated, location-aware marketing and operations. They transform a simple mobile application from a passive content repository into an active, intelligent agent capable of engaging customers at the most opportune moments.
By moving beyond generic messaging and embracing these context-driven triggers, any business can unlock a significant strategic advantage. Implementing these systems is more accessible than ever, with powerful APIs and platforms available from providers like Google Maps Platform, Mapbox, Radar, and the comprehensive geographic information system (GIS) leader Esri, which continues to innovate just down the road from me here in Redlands. The key is to begin with a clear understanding of these fundamental triggers, which serve as the engine for all that follows.